Networking Basics
Tue, Mar 23, 2021 | #networking #tcp #ip #nmap
Some key learnings from TryHackMe Networking Module.
OSI mnemonics
A Penguin Said That Nobody Drinks Pepsi
People Don’t Need Those Stupid Packets Anyways
+---+--------------+--------------------------------------------+--------------------------------------+
+ | OSI Layer | Function | Protocols |
+---+--------------+--------------------------------------------+--------------------------------------+
+ 7 | Application | network process to application | DNS, WWW/HTTP, FTP, POP/SMTP, Telnet |
+ 6 | Presentation | data representation and encryption | HTML, JPEG, MP3 |
+ 5 | Session | interhost communication | RPC, SOCKS, SSL, TLS |
+ 4 | Transport | end to end connection & reliablity | TCP, UDP |
+ 3 | Network | path determination & logical addressing | IP, IPsec, ICMP |
+ 2 | Data Link | physical adressing, packet corruption test | Ethernet, MAC, Fibre channel |
+ 1 | Physical | binary to signal | RJ45, DSL, 802.11 |
+---+--------------+--------------------------------------------+--------------------------------------+
+---+--------------+-----------------------------------------------------------------------------------+
+ | OSI Layer | Encapsulation Process |
+---+--------------+-----------------------------------------------------------------------------------+
+ 7 | Application | / L7 Header / Data (Data) / |
+ 6 | Presentation | / L6 Header / Data (Data / |
+ 5 | Session | / L5 Header / Data (Data) / |
+ 4 | Transport | / L4 Header / Data (Segments/Datagrams) / |
+ 3 | Network | / L3 Header / Data (Packets) / |
+ 2 | Data Link | / L2 Header / Data (Frames) / L2 Trailer / |
+ 1 | Physical | / Data Stream (Bits) / |
+---+--------------+--------------------------------------------+--------------------------------------+
L2 Trailer verifies that the data has not been corrupted on transmission.
+-------------------+-------------+
| TCP/IP | OSI |
+-------------------+-------------+
| Application | Layer 7,6,5 |
| Transport | Layer 4 |
| Internet | Layer 3 |
| Network Interface | Layer 2,1 |
+-------------------+-------------+
Wireshark:
Physical Layer
Frame 2: 81 bytes on wire (648 bits), 81 bytes captured (648 bits)
Data Link Layer
Ethernet II, Src: IntelCor_76:2c:e4 (0c:8b:fd:76:2c:e4), Dst: HuaweiTe_9e:5d:32
Network Layer
Internet Protocol Version 4, Src: 172.16.16.77, Dst: 193.60.169.52
Transport Layer
User Datagram Protocol, Src Port: 37578, Dst Port: 53
Application Layer
Domain Name System (query)
Enumeration with nmap
nmap is used for port scanning. It will connect to each port of the target in turn and depending on how the port responds, it can be determined as being open, closed or filtered. Once we know which ports are open, we can then look at enumerating which services are running on each port.
Important switches
-O detect which operating system is running on the target
-Sv detect the version of the services running on the target
-vvv verbose output
-Oa save nmap results in three major formats
-On save results in "normal" format
-Og save results in "grepable" format
-A agressive mode : service detection, os detection, traceroute, common script scanning
-T5 timing template to level 5
-p 80 scan only port 80
-p 1000-1500 scan ports 1000-1500
-p- scan all ports (takes very long .. speedup with -T5)
--script activate script
-sT TCP Scan
-sU UDP Scan
-sS Syn Scan
-Pn Treat all hosts as online -- skip host discovery => Bypass ICMP block
-sn Ping Scan - disable port scan
TCP Scan
TCP scan perform a full three way handshake.
Client Target
| SYN |
|----------->|
| |
| SYN/ACK |
|<-----------|
| |
| ACK |
|----------->|
| |
Succesful TCP Handshake in Wireshark:
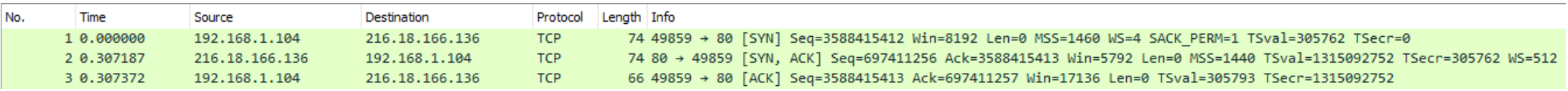
If a port is closed the server sends back RST (reset) instead of SYN/ACK. If the port is filtered by firewall then the TCP SYN packet is either dropped, or spoofed with a TCP reset. Where TCP scans perform a full three-way handshake with the target, SYN scans sends back a RST TCP packet after receiving a SYN/ACK from the server (this prevents the server from repeatedly trying to make the request) => SYN scan = “half open” scan = “stealth” scan
Client Target
| SYN |
|----------->|
| |
| SYN/ACK |
|<-----------|
| |
| RST |
|----------->|
| |
Closed Port in Wireshark:
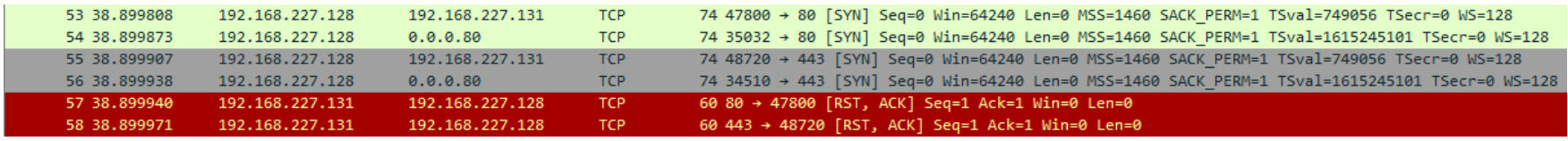
SYN scan pros:
- bypass older intrusion detection systems as they are looking out for a full three way handshake
- SYN scans are referred to as “stealth” scans because most applications only log fully established connections
- faster than standard tcp scans due to the incomplete connection
SYN scan cons:
- SYN scans require the ability to create raw packets => sudo permissions required
- unstable services are sometimes brought down by SYN scans
ICMP Network scanning
If we want to determine which ip address is assigned to an active host we can scan the network with a ping sweeper.
Ping sweep on 172.16.x.x network (netmask: 255.255.0.0) : nmap -sn 172.16.0.0/16
Firewall evasion
switch description
-Pn Treat all hosts as online -- skip host discovery => Bypass ICMP block
-f fragment packets making less likely that the packets will be detected by a firewall or IDS
--mtu <number> like -f but we have control over the size of the packets
--scan-delay <ms> can be used for evading any time-based firewall/IDS triggers or unstable networks
--badsum determines the presence of a firewall/IDS through sending packets with invalid TCP/UDP checksums.
nmap hot tips
If your nmap scan takes a while you can check the scan progress with any key except {vdp?}.
v / V : decreases / increases verbosity level
d / D : decrease / increase debug level
p / P : turn on / off packet tracing
? : print a runtime interaction help screen