Tamper Linux Shells
Sun, Jul 31, 2022 | #linux #shell #pi
Today I installed Kali Linux on my Raspberry Pi to tackel a reverse engineering book that has been collecting dust at home for some time now.
After setting up SSH access via the Pi GUI, I wondered how to control existing shells by using an SSH session.
Kill local shell from remote shell
┌──(kali㉿kali-raspberry-pi)-[~]
└─$ ps -aux | egrep "zsh|qt" // find correct pts (pseudo terminal slave)
kali 1174 0.5 9.8 411164 91908 ? Sl 11:27 0:05 /usr/bin/qterminal
kali 1232 0.5 0.7 13612 6860 pts/0 Ss+ 11:27 0:05 /usr/bin/zsh
kali 3676 0.9 0.6 10284 5900 pts/2 Ss 11:36 0:05 -zsh
kali 6402 0.0 0.2 6076 1936 pts/2 R+ 11:46 0:00 grep -E --color=auto zsh|qt
┌──(kali㉿kali-raspberry-pi)-[~]
└─$ sudo kill -9 1232 1174
Write to local shell from remote shell
┌──(kali㉿kali-raspberry-pi)-[~]
└─$ ps -aux | egrep "zsh|qt"
kali 1125 2.1 12.4 436656 116284 ? Sl 10:04 0:11 /usr/bin/qterminal
kali 1190 1.0 0.6 10492 5712 pts/0 Ss+ 10:04 0:05 /usr/bin/zsh
kali 2241 2.9 0.6 10388 5768 pts/1 Ss 10:08 0:09 -zsh
kali 3748 0.0 0.1 6140 1856 pts/1 S+ 10:13 0:00 grep -E --color=auto zsh|qt
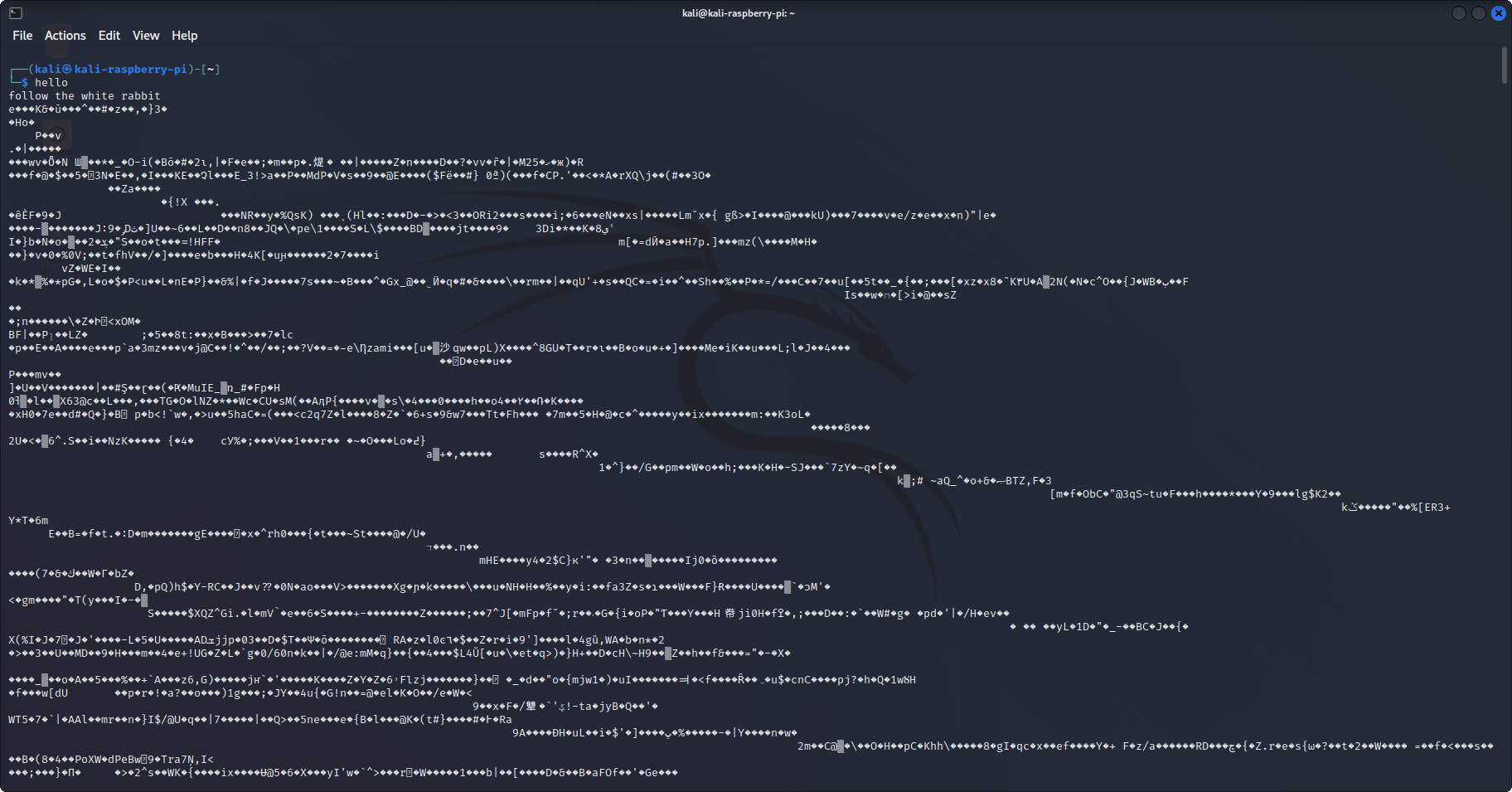
┌──(kali㉿kali-raspberry-pi)-[~] // greetings from another shell
└─$ echo 'hello' > /dev/pts/0
┌──(kali㉿kali-raspberry-pi)-[~] // send message
└─$ echo 'follow the white rabbit' > /dev/pts/0
┌──(kali㉿kali-raspberry-pi)-[~] // go wild
└─$ cat /dev/urandom > /dev/pts/0
^C
Capture input stream
┌──(kali㉿kali-raspberry-pi)-[~]
└─$ cat < /dev/pts/1 // makes shell unstable
OAOAtsAOAOAAOAOAAOAOAAOAOABOAOAAOAOAAOBOAAOAOAAOAOABOAOAAOBOAAOAOBAOAOABOAOABOBOAAOAOBBOAOAAOBOBAOAOABOBOAAOAOBBOAOAAOBOBAOAetC^C